What the Collins Aerospace Cyberattack Reveals About the Fragility of Digital Supply Chains
On 20 September 2025, Europe’s airports fell silent.
From Heathrow to Berlin, check-in desks froze. Baggage systems failed. Passengers stood in queues stretching out the terminal doors. Flights were cancelled by the hundreds. Brussels Airport told airlines to abandon half of all scheduled departures.
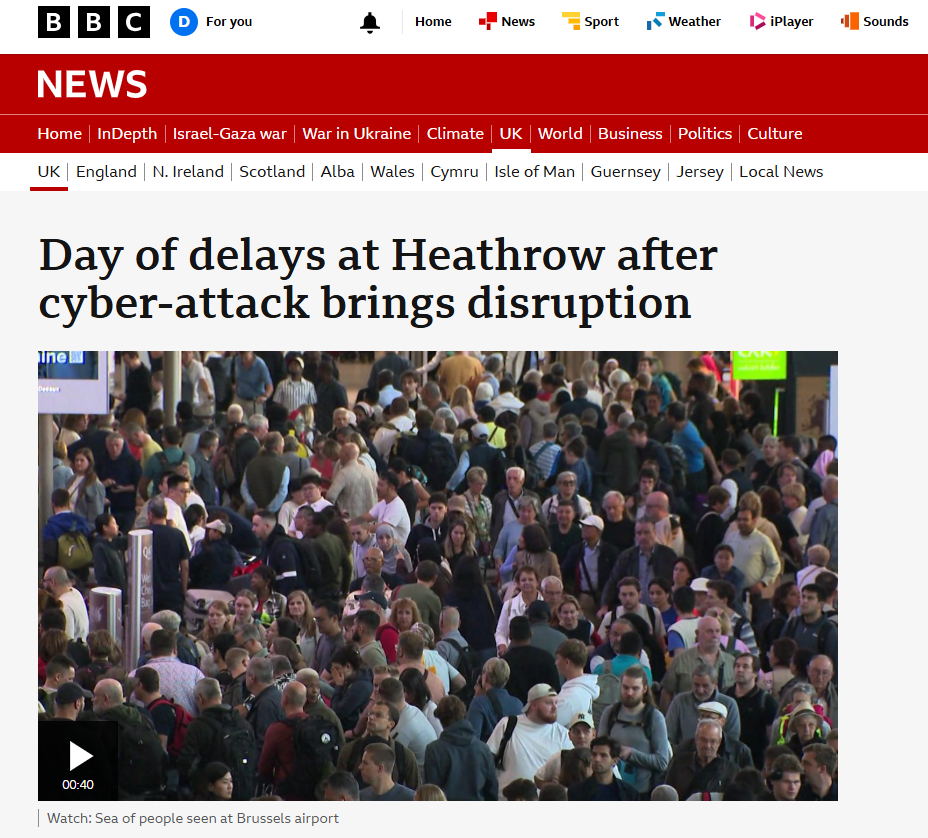
The cause?
A cyberattack on a single software platform used by dozens of airports and airlines across Europe: MUSE, operated by Collins Aerospace.
And just like that, a digital bottleneck became a physical crisis.
📞 Speak to Bondgate IT
Do you know which of your systems are critical? And do you know how resilient they are? If not, now is the time to act.
Book a Cyber Resilience Review Call 01325 369 950What the Collins Aerospace cyberattack Tells Us About Digital Fragility
Collins Aerospace, a division of RTX (formerly Raytheon Technologies), supplies mission-critical aviation software. Their MUSE platform handles key functions like electronic check-in, baggage handling, and flight boarding for major airports.
In the early hours of 20 September, MUSE went offline after what investigators later confirmed was a targeted cyberattack. Early suspicions of foreign interference gave way to signs pointing toward a domestic group exploiting a vulnerability in the system’s authentication layer.
With no working software, airports were forced into manual fallback procedures, handwritten boarding passes, radio communication between gates, and delayed or missing luggage.
💬 “It was like stepping back into 1985,” one airline operations manager said.
The impact was immediate and severe. By mid-morning, hundreds of flights were cancelled, thousands of passengers stranded, and losses running into millions.
What Went Wrong
This wasn’t bad luck. The Collins Aerospace cyberattack revealed three systemic failures:
- No Redundancy
Despite being mission-critical, MUSE had no active backup. When it failed, there was nothing to switch over to. - Weak Fallback Planning
Many airports had never tested a full manual recovery scenario. Staff improvised in real time, with predictable chaos. - Governance Blind Spots
Collins is a household name in aviation, but scale did not guarantee resilience. There was no transparent governance framework guiding how MUSE handled information security, supply chain dependencies, or incident response.
This was a failure of preparation as much as it was a breach.
Why This Isn’t Just Aviation’s Problem
It’s tempting to think this is an aviation-only issue. But here’s the reality: every business has a MUSE.
Your MUSE might be:
- Your cloud-based payroll system.
- Your CRM platform.
- Your ERP or supplier portal.
- The logistics software that manages your supply chain.
If one of those systems fails, really fails, how ready are you?
Because when clients can’t be billed, suppliers can’t be paid, or staff can’t access systems, it’s not your vendor who takes the blame. It’s you.
The Collins Aerospace cyberattack is a stark reminder that supply chain resilience is a universal business issue.
The Role of EASA Part-IS
Aviation at least has a framework. The European Union Aviation Safety Agency (EASA) mandates Part-IS requiring operators and suppliers to run an Information Security Management System (ISMS) aligned with aviation risk.
Part-IS includes:
- Defined scope covering assets and suppliers.
- Clear policies with board-level accountability.
- Risk assessments and incident response planning.
- Continuous monitoring and improvement.
The Collins Aerospace cyberattack demonstrates why this matters. Without structured governance, even industry giants can become single points of failure.
Outside aviation, few industries have a Part-IS equivalent. SMEs can still align with frameworks like Cyber Essentials Plus or ISO 27001, which provide similar protection and reassurance.an they shouldn’t.
For SMEs, frameworks like Cyber Essentials Plus and ISO 27001 offer a practical route to comparable resilience.
SME Lessons from the Collins Aerospace cyberattack
For the Frustrated Finance Director
Your pain is unpredictability. Outages and breaches don’t just cause downtime, they drive unexpected costs. These may include regulatory fines, lost contracts, reputational damage, or higher insurance premiums.
The Collins incident proves that financial exposure from weak governance can run into the millions. Investing in structured resilience is not wasted cost; it’s protection for predictable cash flow and accurate budgeting.
Lesson: Treat cyber resilience as financial risk management, not an optional IT expense.
For the Overwhelmed Managing Director
Your challenge is growth. You need systems to work smoothly while you focus on strategy. But growth stalls the moment operations grind to a halt.
The lesson here is that resilience is not just an IT issue. It’s a board-level responsibility. Your job is to ensure continuity, protect reputation, and reassure stakeholders that risks are being managed.
Lesson: Build cyber resilience into your strategy and hold suppliers accountable.
For the Stretched Office Manager
When systems fail, your phone rings first. Staff expect you to fix it, even if the problem sits with a third-party provider.
The takeaway from Collins is the importance of fallback planning. In aviation, that meant handwritten boarding passes. In your world, it might mean knowing how to issue invoices manually or access critical records offline.
Lesson: Don’t wait for a failure to figure out your Plan B. Document, train, and test fallback processes now.
📞 Ready to Strengthen Your Business Resilience?
Bondgate IT works with organisations across Tees Valley and the UK to build resilience with governance, culture, and planning, not just tools.
Book a Consultation Call 01325 369 950Practical Steps Every SME Can Take
Here are five immediate actions to strengthen your resilience:
- Audit Critical Suppliers
Identify who you rely on most. Ask for evidence of their security and continuity planning. - Put Governance on the Agenda
Cyber resilience belongs in the boardroom, not just the IT helpdesk. Assign accountability at executive level. - Test Your Fallbacks
Run tabletop exercises. Simulate system outages. See what breaks, and fix it. - Invest in Layered Defences
Antivirus and firewalls alone are not enough. Use endpoint detection, secure backup, MFA, and continuous monitoring. - Adopt a Framework
Whether Part-IS, ISO 27001, or Cyber Essentials Plus, structured frameworks force discipline and provide assurance to clients and regulators.
The Takeaway
The Collins Aerospace cyberattack will be remembered not just for grounded flights, but for what it revealed: the fragility of digital supply chains.
When one supplier fails, the impact ripples far beyond their systems.
For every SME in the North East and beyond, the key question is this: if your critical supplier fails tomorrow, how long can you survive?
The only defence is governance, resilience, and preparation.
How Bondgate IT Helps
At Bondgate IT, we help businesses across the North East strengthen resilience. We don’t just implement tools; we embed governance, culture, and planning. That means:
- Clear visibility of critical suppliers.
- Structured incident response plans.
- Tested fallback processes.
- Independent frameworks like Cyber Essentials Plus and ISO 27001.
Our mission is simple: to make sure your business doesn’t find itself “grounded” by someone else’s failure.
📞 Ready to review your digital supply chain resilience?
- Call us on 01325 369 950.
- Visit www.bondgate.co.uk.
