Are you an aviation SME staring down the barrel of EASA Part-IS compliance, picturing mountains of paperwork, endless audits, and budget-busting consultants? I understand. The idea of implementing an Information Security Management System (ISMS) can feel daunting, especially when resources are stretched thin. My experience tells me that many small businesses fear “overkill” building a system far too complex and costly for their actual needs.
This article is designed to cut through that fear. We’ll explore why an ISMS is essential for Part-IS, but more importantly, how to build one that’s right-sized for your aviation business effective, compliant, and without unnecessary bureaucracy. You’ll get a step-by-step guide to defining scope, managing risks, implementing key controls, and maintaining your system efficiently. By the end, you’ll see that Part-IS compliance, far from being a burden, can be achieved with a smart, practical approach that benefits your business.
🎯 Book a Free 30-Minute Strategy Call
Speak to one of our specialists about how Bondgate IT can help on your compliance journey.
Book My CallWhy Your SME Needs an ISMS for EASA Part-IS Compliance
An Information Security Management System (ISMS) is more than just a collection of security tools; it’s a systematic approach to managing sensitive company information so that it remains secure. For EASA Part-IS compliance, having a documented and functioning ISMS is not optional – it is a core requirement. Part-IS mandates that organisations establish, implement, maintain, and continually improve an ISMS for information and communication technology (ICT) systems which, if compromised, could endanger aviation safety.
Why is this so crucial for SMEs? Because even small organisations handle critical data and rely on digital systems that are vital to their operations and safety. A breach in a small MRO’s system, for instance, could impact the airworthiness of aircraft. An ISMS provides the framework to identify these risks, put controls in place to mitigate them, and ensure your team understands their role in protecting your digital assets. It shifts security from a reactive measure to a proactive, integrated part of your business strategy.
The Dangers of Overkill: Keep Your ISMS Simple and Effective
The biggest fear we encounter with ISMS implementation, especially among SMEs, is the perceived need for a sprawling, bureaucratic system. Many envision binders full of policies nobody reads and complex procedures that slow down operations. This is a common pitfall.
The key to successful Part-IS compliance, particularly for smaller firms, is avoiding overkill.
An ISMS should be proportionate to your organisation’s size, complexity, and the criticality of the information and systems it protects. Building a giant, unwieldy system for a small operation is not only wasteful but often counterproductive; it becomes difficult to maintain, understand, and use effectively. Our approach is always to help you build a right-sized ISMS – one that meets regulatory requirements, genuinely enhances your security, and integrates smoothly into your existing workflows without becoming a burden.
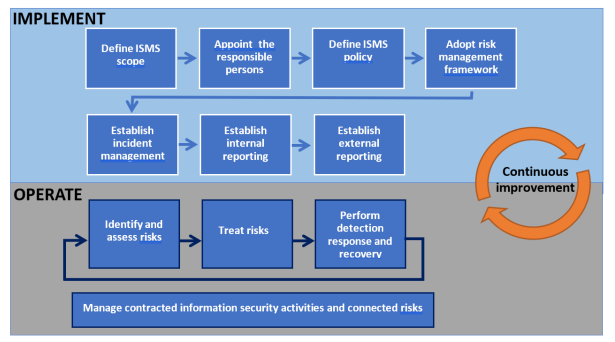
Step 1: Define the Scope of Your ISMS (Focus on What Matters)
The very first and most critical step in building your ISMS is defining its scope. This means clearly identifying what your ISMS will cover. Don’t fall into the trap of trying to secure everything at once. Part-IS focuses on ICT systems that could affect aviation safety.
Ask yourself:
- Which of our systems directly support or impact aviation safety? (e.g., flight planning systems, maintenance records, air traffic control communication systems, operational control systems).
- Which data, if compromised, would have a direct or indirect impact on safety?
- What are the boundaries of these systems? Which departments, physical locations, and even third-party services (like cloud providers) are involved?
By narrowing the scope to what truly matters for Part-IS, you avoid securing non-critical systems that would add unnecessary complexity and cost. This targeted approach makes the entire process more manageable and ensures your resources are focused where they count most.
Step 2: Identify Risks and Prioritise Critical Controls
Once your scope is defined, the next step is to understand the risks to the information and systems within that scope. This doesn’t require a highly complex, academic risk assessment for most SMEs. Instead, focus on a practical approach:
- Identify Threats: What could go wrong? (e.g., cyberattacks like ransomware or phishing, human error, system failures, natural disasters, insider threats).
- Identify Vulnerabilities: What weaknesses do your systems or processes have that these threats could exploit? (e.g., outdated software, weak passwords, lack of staff training).
- Assess Impact: If a risk materialised, what would be the impact on safety, operations, finances, and reputation?
- Prioritise: Not all risks are equal. Focus your efforts on the high-impact, high-likelihood risks first.
Based on your risk assessment, you then select and prioritise controls. These are the safeguards you put in place to reduce identified risks to an acceptable level. Keep it practical and proportionate.
Step 3: Implement Key Security Measures Without Unnecessary Complexity
This is where you put your chosen controls into action. EASA Part-IS requires a range of security measures, but these don’t have to be overly complicated for an SME. Focus on fundamentals that address your identified risks:
- Access Control: Ensure only authorised personnel can access critical systems and data. This includes strong password policies, multi-factor authentication (MFA), and restricting access based on job roles.
- Data Backups and Recovery: Regularly back up all critical data and ensure you have a clear plan for restoring it quickly in case of a cyberattack or system failure.
- Incident Response Plan: Develop a simple, actionable plan for what to do if a security incident occurs. Who do you call? What are the first steps? How do you report it?
- Network Security: Implement firewalls, secure network configurations, and segmentation to protect critical systems from unauthorised access.
- Endpoint Protection: Use antivirus and anti-malware software on all devices accessing critical systems.
The emphasis here is on effectiveness, not complexity.
Step 4: Train Your Team and build a Security Culture
Your people are your strongest defence, or your weakest link. EASA Part-IS explicitly requires organisations to provide security awareness training to all relevant personnel. This is not a one-off lecture; it’s about fostering a continuous security-conscious culture.
- Regular Training: Conduct regular, engaging training sessions that are relevant to your employees’ roles. Use real-world examples and avoid jargon.
- Phishing Simulations: Periodically run simulated phishing attacks to test your team’s vigilance and reinforce training.
- Open Communication: Encourage employees to report suspicious activities without fear of blame. Make it easy for them to ask questions and report concerns.
This human element is perhaps the most cost-effective defence against cyber threats. For more in-depth guidance on this vital aspect, our article Cybersecurity Awareness in Aviation: Your Frontline ISMS Defence provides a deeper dive.
Step 5: Document, Monitor, and Improve
An ISMS is a living system. Part-IS requires it to be maintained and continually improved. For SMEs, this doesn’t mean mountains of paperwork, but rather smart, efficient processes:
- Essential Documentation: Document your ISMS scope, policies, risk assessments, and key procedures. Keep it concise and easy to understand.
- Monitoring: Regularly review your security controls and monitor for incidents. This can be as simple as reviewing logs or conducting periodic checks.
- Internal Audits: Conduct internal audits periodically to ensure your ISMS is working as intended and identify areas for improvement.
- Management Review: Senior management should regularly review the performance of the ISMS and make decisions about its ongoing development.
The goal is to demonstrate that you have a structured approach and are continually enhancing your security posture.
Leverage Cyber Essentials or ISO 27001 to Streamline Compliance
You don’t have to start from scratch. Existing cybersecurity frameworks can significantly streamline your path to Part-IS compliance:
- Cyber Essentials: For UK-based SMEs, achieving Cyber Essentials or Cyber Essentials Plus is an excellent starting point. It covers fundamental controls (firewall, secure configuration, user access control, malware protection, patch management) that align well with basic Part-IS requirements. It’s a rapid, cost-effective way to establish a baseline of security hygiene.
- ISO 27001: While more comprehensive and designed for certification, ISO 27001 provides a robust framework for building a full ISMS. Its structured approach to risk management and control implementation can greatly assist in meeting Part-IS’s broader ISMS requirements.
Both frameworks offer a structured path and can demonstrate a commitment to information security that aligns with EASA’s expectations. If you’re unsure which one is right for your organisation, or how they compare to Part-IS, our detailed comparison in Cyber Essentials vs ISO 27001 vs EASA Part-IS: What’s the Difference? will provide clarity. Remember, your IT provider is also part of your supply chain; ensure they understand your needs and help you manage third-party risks. For more on this, consider our insights on Supply Chain Cyber Risk in Aviation — And How to Manage It.
Building an ISMS for EASA Part-IS compliance doesn’t have to be overwhelming. By focusing on a proportionate, risk-based approach, you can create a system that truly protects your aviation business, meets regulatory demands, and avoids unnecessary bureaucracy.
