Explore the terrifying world of cybersecurity horror stories this Halloween. Discover the common threats that could haunt your business and learn how to protect it from digital ghouls. Bondgate IT is here to help you defend your business against unseen cyber terrors.
6 Reasons Why Access Management is Essential to Good Data Security
Did you know that the average cost of a data breach in the UK is now £3.6 million? That’s a lot of money to lose, but it’s an even bigger hit to your reputation. A data breach can damage your relationships with customers and partners, and it can take years to recover.
One of the best ways to protect yourself from a data breach is to implement a strong access management system. Access management helps you control who has access to your data and resources, and it can help you detect and respond to suspicious activity quickly.
In this blog post, we’ll discuss six reasons why access management is essential to good data security. We’ll also share tips for implementing a strong access management solution in your organization.
How to Protect Your Business from Classiscam Attacks and Keep Your Data Safe
Classiscam is a fraud-as-a-service platform that allows cybercriminals to easily create and deploy phishing attacks. In H1 2023, Classiscam groups targeted internet users in 79 countries worldwide, impersonating 251 unique brands. Europe was the most targeted region, with 384 individual schemes.
How to Spot and Protect Yourself from Fake LinkedIn Sales Bots with a Multi-Layered Approach to Security
How to spot and protect yourself from fake LinkedIn sales bots with a multi-layered approach to security. Learn the signs of a fake profile, what to do if you receive a suspicious message, and how to keep your account safe.
How to Prepare Your Business for Business Continuity and Disaster Recovery (BCDR)
Small businesses face a lot of risks, from natural disasters to cyber-attacks. That’s why it’s so important to have a plan in place for business continuity and disaster recovery (BCDR). Learn from Bondgate IT the 10 essential tips to keep your business running smoothly, even in the event of an unexpected event.
How AI is Revolutionizing Cybersecurity
Artificial intelligence (AI) is transforming cybersecurity in a number of ways. AI-powered solutions can help businesses detect and prevent threats, automate incident response, and improve overall security posture. In this blog post, we explore the latest developments in AI cybersecurity and how businesses can benefit from this technology.
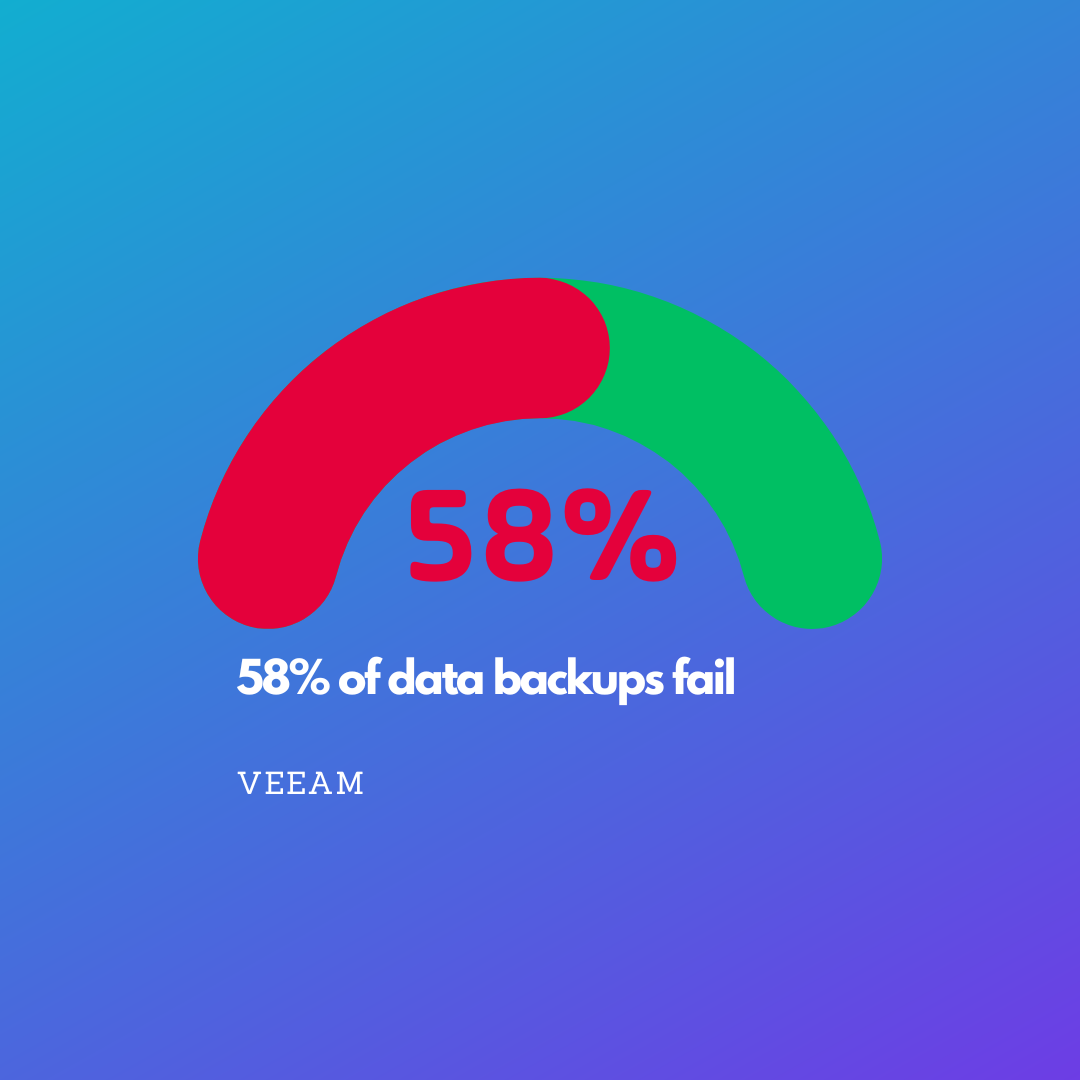
The Death of Backups: Protecting Your Business with BCDR
Is your business at risk with 58% of data backups failing? As the Director of Operations at Bondgate IT, I’ve seen businesses relying solely on backups to protect their valuable data. But here’s the hard truth: backups alone are pointless. Yes, they preserve your data, but they don’t guarantee a quick recovery after a disaster. That’s where BCDR steps in to save the day!
Achieving ISO 27001 and ISO 9001: Delivering Customer Satisfaction and Robust Security at Bondgate IT
Bondgate IT is proud to announce our recent attainment of ISO 27001 and ISO 9001 certifications. These certifications highlight our commitment to customer satisfaction and comprehensive security measures. Learn how our multi-layered approach to security and focus on quality management benefit our customers. Discover the significance of ISO 27001 and ISO 9001 in ensuring top-quality services.
Secure Your Business with Bondgate IT’s Multilayered Cybersecurity Approach: MDR, SOC, and SIEM
Learn how Bondgate IT’s multilayered cybersecurity approach, including MDR, SOC, and SIEM, can provide robust protection for your business against evolving cyber threats. Contact us for a cybersecurity consultation.